
Recommended Security Measures to Protect Your Servers
Learn essential server security measures to protect against breaches: access control, firewalls, patching, monitoring, and hardening best practices fo...

Learn essential server security measures to protect against breaches: access control, firewalls, patching, monitoring, and hardening best practices fo...
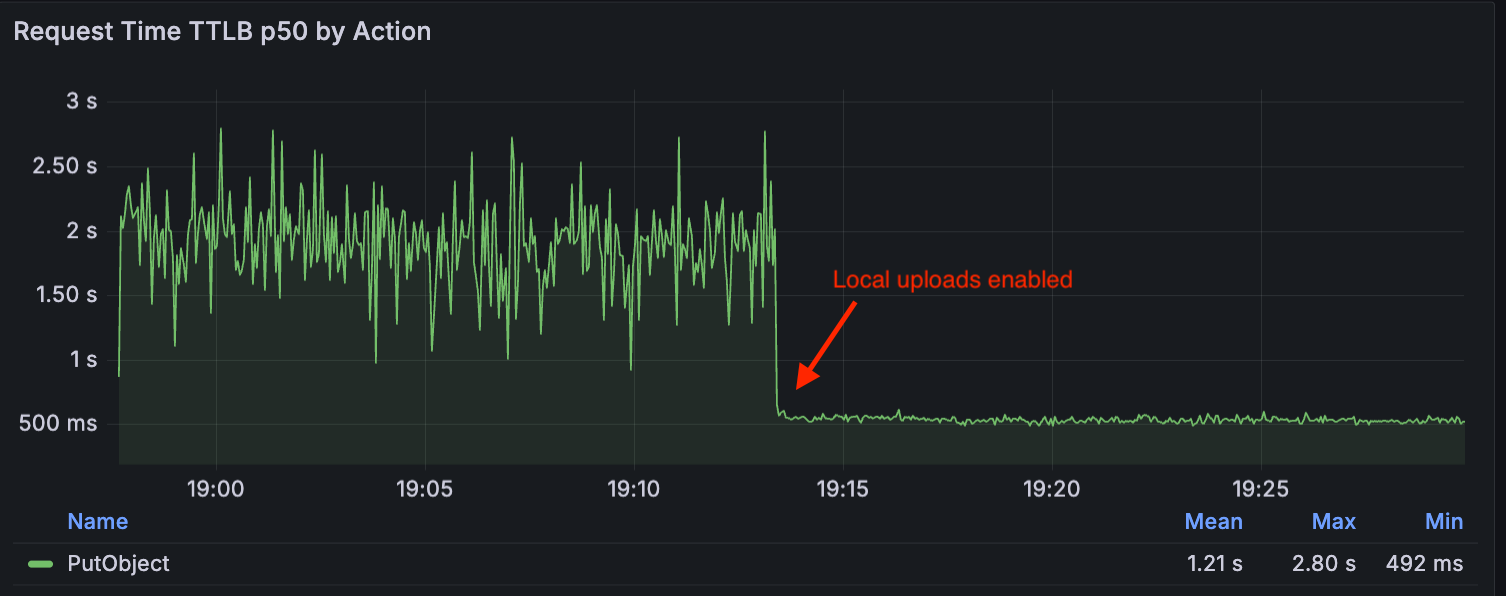
Local Uploads on R2 reduces request duration for uploads by up to 75%. It writes object data to a nearby location and asynchronously copies it to your...
Learn how to use Gemini CLI to bring Google's AI-powered coding assistance into your terminal for faster code analysis, debugging, and fixes.
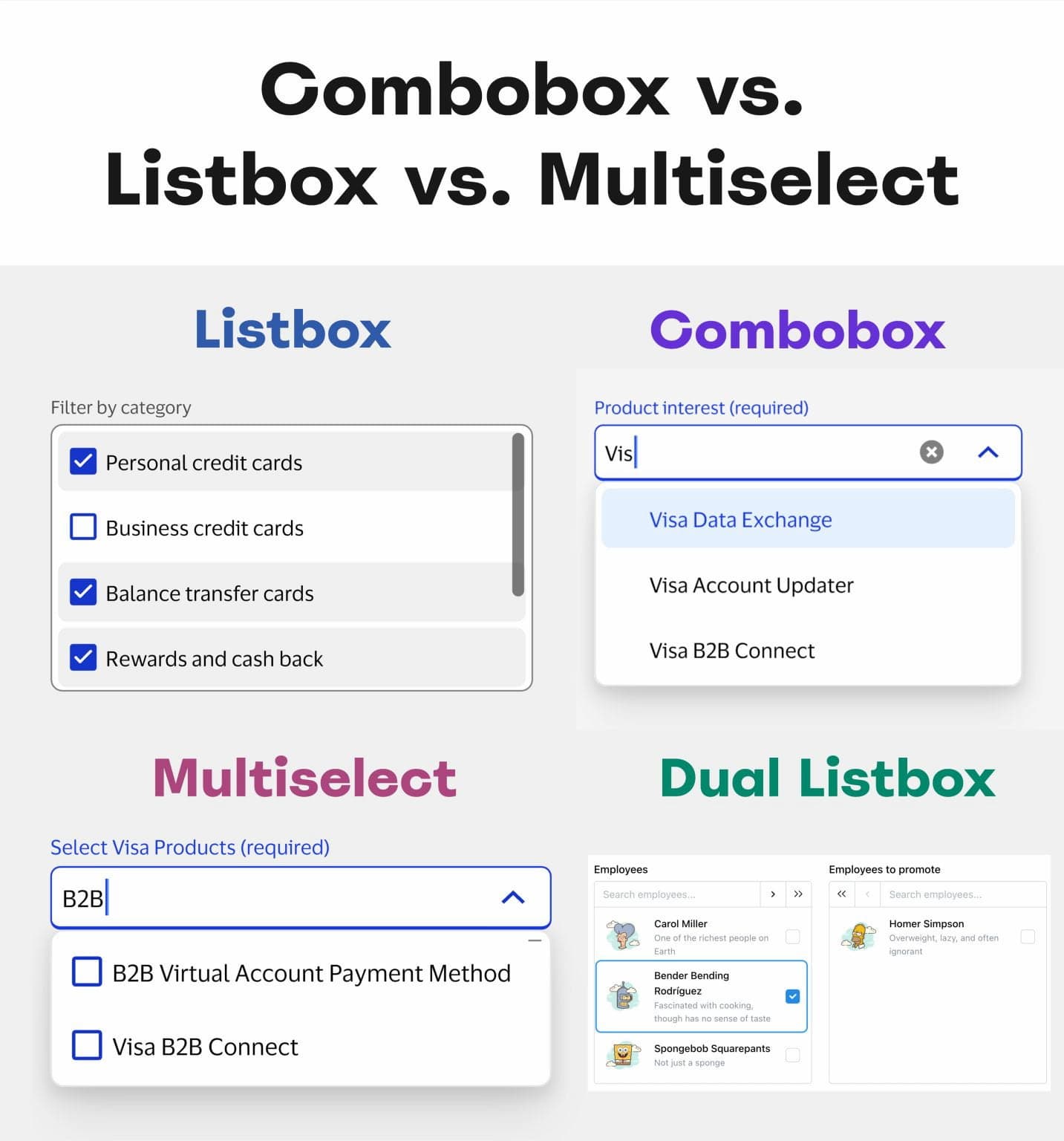
Combobox vs. Multi-Select vs. Listbox vs. Dual Listbox? How they are different, what purpose they serve, and how to choose the right one. Brought to y...
We will explore one of the biggest problems in the fields of Machine Learning and Deep Learning: the struggle of loading and handling different types...
In the standard Kubernetes model, a node’s suitability for workloads hinges on a single binary "Ready" condition. However, in modern Kubernetes enviro...

Install and secure phpMyAdmin on Ubuntu with step-by-step instructions. Secure MySQL databases with SSL/TLS and Apache authentication.

#771 — February 3, 2026 Read on the Web JavaScript Weekly Four Heavyweights Drop Updates Four stalwarts of the JavaScript ecosystem all shipped notab...
Jason Willems believes the tech monoculture is finally breaking, Don Ho shares some bad Notepad++ news, Tailscale's Avery Pennarun pens a great downti...

Over the past week, we passed Laba festival, a traditional marker in the Chinese calendar that signals the final stretch leading up to the Lunar New Y...

We’ve released an open library of Agent Skills to help teams build and manage infrastructure faster with AI.
A senior engineer's guide to architecting and extending Copilot's real-world applications. The post How to maximize GitHub Copilot’s agentic capabilit...

A prolific data ransom gang that calls itself Scattered Lapsus ShinyHunters (SLSH) has a distinctive playbook when it seeks to extort payment from vic...

I've always thought that creating a VS Code theme was a lot of work. But lo and behold, it took less than six hours to get it working, then a day or t...

Learn your way around the Python terminal. You’ll practice basic commands, activate virtual environments, install packages with pip, and keep track of...

Learn how to install Java (JRE & JDK) on Ubuntu using apt. Step-by-step guide to setting up Java, verifying installation, and managing multiple versio...
Learn how to open ports in Linux using iptables, ufw, and firewalld. This guide covers checking open ports, security best practices, and troubleshooti...

Let’s make the most of the shortest month of the year with a new collection of desktop wallpapers that are sure to bring a smile to your face — and ma...
We introduced Docker Sandboxes in experimental preview a few months ago. Today, we’re launching the next evolution with microVM isolation, available n...
We discuss the buzz around Clawdbot / MoltBot / OpenClaw, how app subscriptions are turning into weekend hacking projects, why SaaS stocks are crashin...
Showing 641 - 660 of 1268 articles