How to Build Your Own Custom LLM Memory Layer from Scratch
Step-by-step guide to building autonomous memory retrieval systems The post How to Build Your Own Custom LLM Memory Layer from Scratch appeared first...
Step-by-step guide to building autonomous memory retrieval systems The post How to Build Your Own Custom LLM Memory Layer from Scratch appeared first...
The US National Reconnaissance Office has declassified information about a fleet of spy satellites operating between 1971 and 2006. I’m actually impre...
The case against pre-built tools in Agentic Architectures The post Plan–Code–Execute: Designing Agents That Create Their Own Tools appeared first on T...
An innovative approach to discovering, analyzing, and governing identity usage beyond traditional IAM controls. The Challenge: Identity Lives Outside...
Many incident response failures do not come from a lack of tools, intelligence, or technical skills. They come from what happens immediately after det...

'Learn what self-learning AI agents are, how they work, and why they matter. This overview explains core concepts, architecture, and tools in simple t...
aside_block <ListValue: [StructValue([('title', 'NOTE'), ('body', <wagtail.rich_text.RichText object at 0x7fe762695850>), ('btn_text', ''), ('href', '...
Microsoft has warned that information-stealing attacks are "rapidly expanding" beyond Windows to target Apple macOS environments by leveraging cross-p...
The Eclipse Foundation, which maintains the Open VSX Registry, has announced plans to enforce security checks before Microsoft Visual Studio Code (VS...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a critical security flaw impacting SolarWinds Web Help Desk (WHD) to...
Every time execution models change, security frameworks need to change with them. Agents force the next shift. The Unattended Laptop Problem No develo...

🚀 Frontend Focus #727 — February 4, 2026 | Read on the web The Too Early Breakpoint — Ahmad thinks we're collapsing to single-column layouts way too...

Python 3.14.3 is now available! Two snakes enjoying a pie with 3.14 on the top and π crimping 538×507 110 KB This is third maintenance release of Pyth...
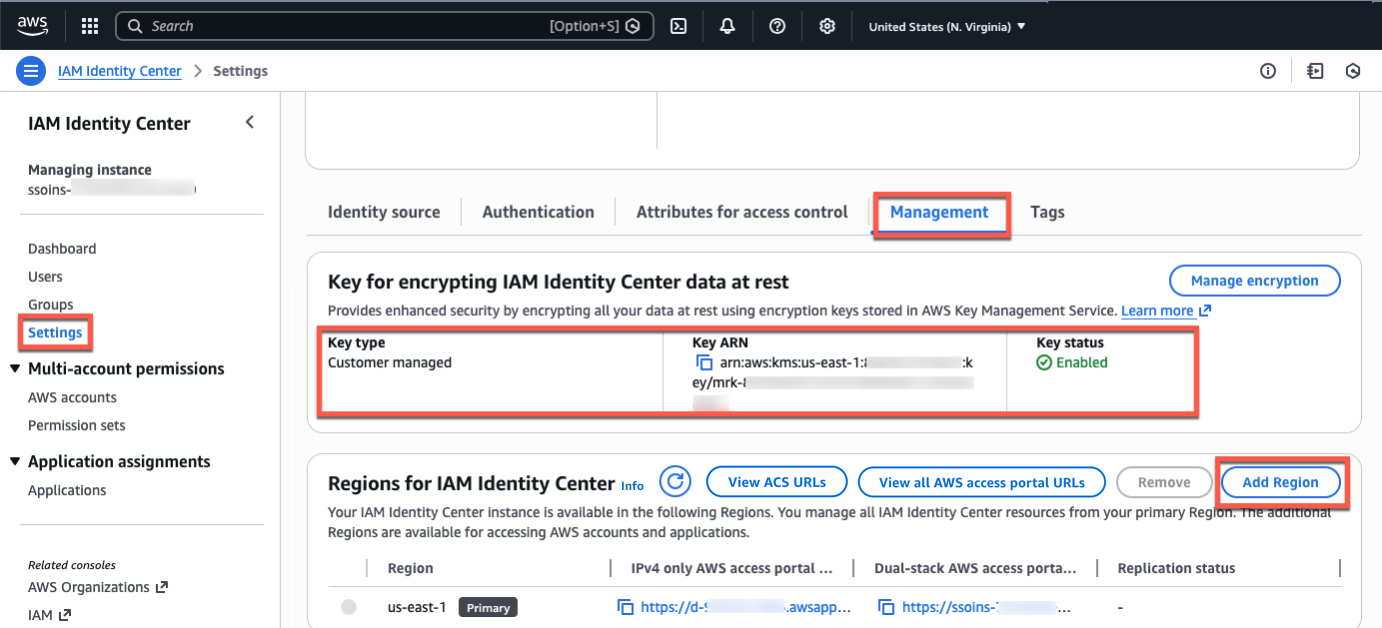
AWS IAM Identity Center now supports multi-Region replication of workforce identities and permission sets, enabling improved resiliency for AWS accoun...
Find out how HashiCorp Vault, HCP Vault Radar, and HCP Boundary can help you fulfill the PCI DSS 4.0 requirements checklist and get compliance certifi...

What languages are growing fastest, and why? What about the projects that people are interested in the most? Where are new developers cutting their te...
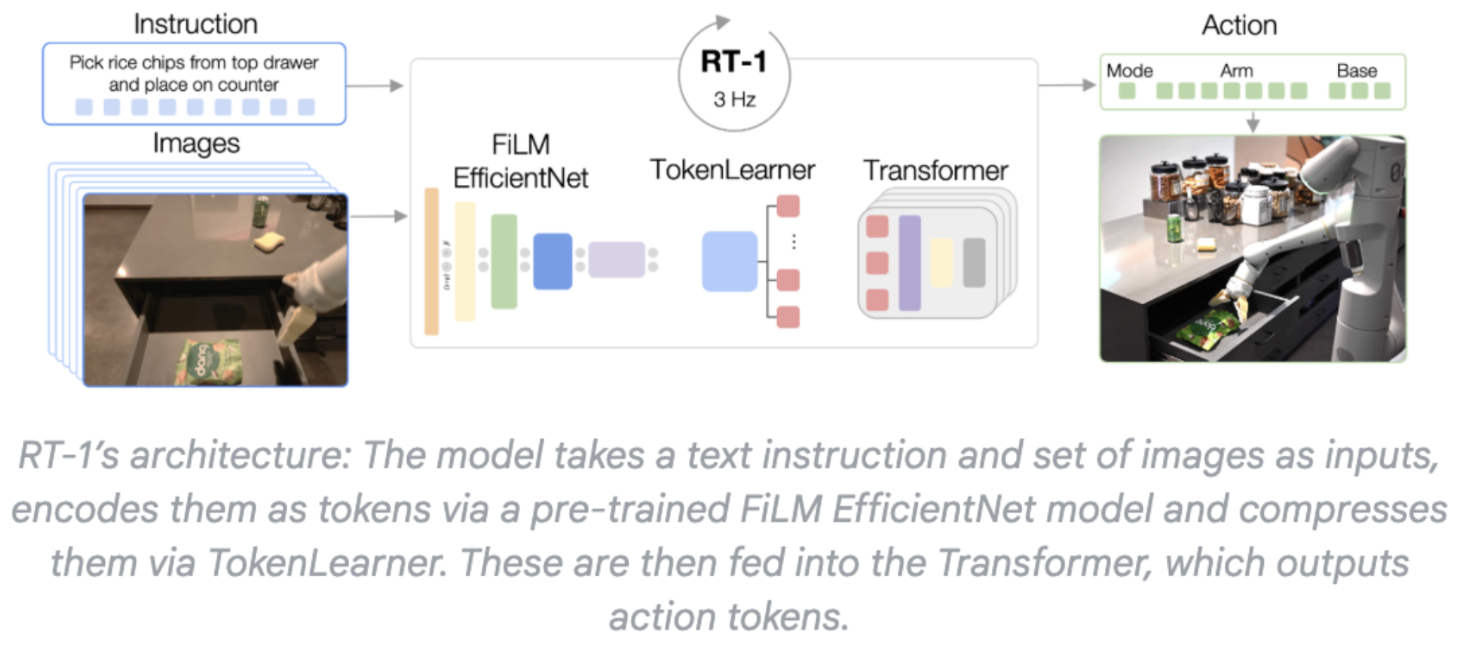
'Explore Vision-Language-Action (VLA) model advancements like Robotic Transformer-1 and \-2, OpenVLA, and π0 (Pi-zero).'
Cybersecurity researchers have disclosed details of a now-patched security flaw impacting Ask Gordon, an artificial intelligence (AI) assistant built...

You’d think that publishing a VS Code extension is an easy process, but it’s not. You have to publish your theme in at least two places. No Hassle Vis...
Learn how to configure Nginx access and error logs and set up log rotation on Ubuntu to prevent disk issues and improve monitoring.
Showing 621 - 640 of 1268 articles