Asian State-Backed Group TGR-STA-1030 Breaches 70 Government, Infrastructure Entities
A previously undocumented cyber espionage group operating from Asia broke into the networks of at least 70 government and critical infrastructure orga...
A previously undocumented cyber espionage group operating from Asia broke into the networks of at least 70 government and critical infrastructure orga...
404Media is reporting that the FBI could not access a reporter’s iPhone because it had Lockdown Mode enabled: The court record shows what devices and...
How much of your AI agent's output is real data versus confident guesswork? The post Prompt Fidelity: Measuring How Much of Your Intent an AI Agent Ac...
What are ways to improve how you're using GitHub? How can you collaborate more effectively and improve your technical writing? This week on the show,...

Learn how to install an SSL/TLS certificate from a commercial certificate authority on Apache or Nginx: CSR creation, chain installation and verificat...
As you know, enterprise network security has undergone significant evolution over the past decade. Firewalls have become more intelligent, threat dete...
Cybersecurity researchers have discovered a new supply chain attack in which legitimate packages on npm and the Python Package Index (PyPI) repository...
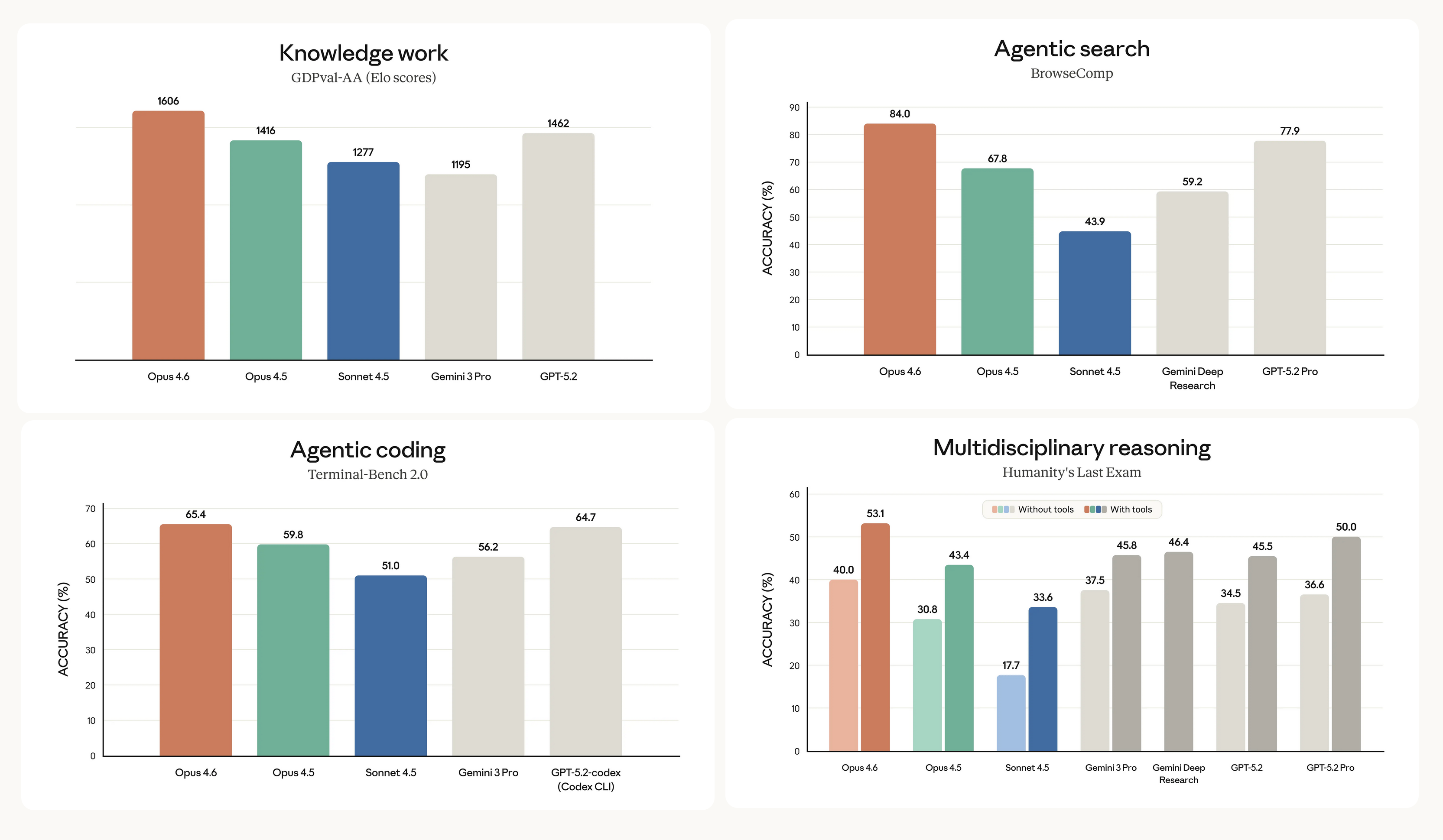
Artificial intelligence (AI) company Anthropic revealed that its latest large language model (LLM), Claude Opus 4.6, has found more than 500 previousl...
'In this tutorial, we demonstrate the power of the latest Claude Opus model with a real coding project using Claude Code and DigitalOcean Gradient'
Learn how to create a new user with sudo privileges on Rocky Linux, including secure configuration, group assignment, and permission verification.

Learn how to deploy and scale a Node.js application with MongoDB on Kubernetes using Helm, including replicas and autoscaling.

#461 — February 6, 2026 Read on the Web React Status Debugging React with AI: Can It Replace a Senior Dev? — A lightning rod topic deftly handled by...
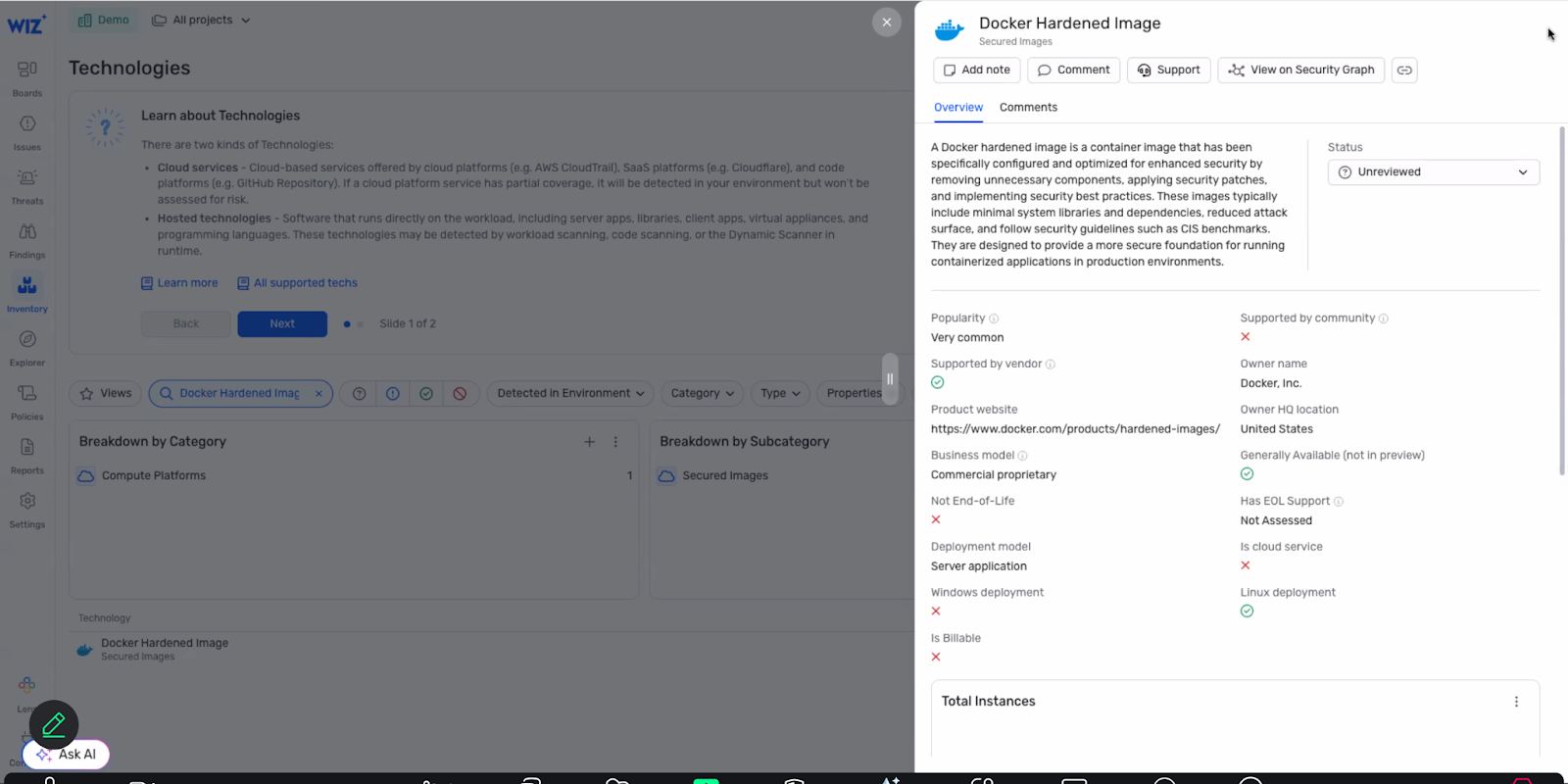
Open source components power most modern applications. A new generation of hardened container images can establish a more secure foundation, but even...

Deepika Manglani, VP of Product at the LA Times, talks about how she’s bringing the 140-year-old institution into the future. The post LaunchPod: Usin...

Stop losing action items in meetings. Granola AI notepad captures your notes, extracts tickets and decisions, and eliminates post-meeting friction for...

Configure preferred endpoints to control how Boundary selects target addresses and avoid failed connections.

At Google Cloud, we’re committed to providing customers with the leading selection of models to build and scale production-ready AI apps and agents on...

Minimal doesn’t always mean usable. This comparison shows how Linear-style UI keeps contrast, affordances, and structure intact, unlike brutalism’s ex...
The distributed denial-of-service (DDoS) botnet known as AISURU/Kimwolf has been attributed to a record-setting attack that peaked at 31.4 Terabits pe...
Sorting through the good, bad, and ambiguous aspects of vibe coding The post TDS Newsletter: Vibe Coding Is Great. Until It’s Not. appeared first on T...
Showing 561 - 580 of 1268 articles