The Death of the “Everything Prompt”: Google’s Move Toward Structured AI
How the new Interactions API enables deep-reasoning, stateful, agentic workflows. The post The Death of the “Everything Prompt”: Google’s Move Toward...
How the new Interactions API enables deep-reasoning, stateful, agentic workflows. The post The Death of the “Everything Prompt”: Google’s Move Toward...
Cyber threats are no longer coming from just malware or exploits. They’re showing up inside the tools, platforms, and ecosystems organizations use eve...
This is amazing : Opus 4.6 is notably better at finding high-severity vulnerabilities than previous models and a sign of how quickly things are moving...
Why do SOC teams keep burning out and missing SLAs even after spending big on security tools? Routine triage piles up, senior specialists get dragged...
The threat actor known as Bloody Wolf has been linked to a campaign targeting Uzbekistan and Russia to infect systems with a remote access trojan know...
Cybersecurity researchers have called attention to a "massive campaign" that has systematically targeted cloud native environments to set up malicious...
BeyondTrust has released updates to address a critical security flaw impacting Remote Support (RS) and Privileged Remote Access (PRA) products that, i...
OpenClaw (formerly Moltbot and Clawdbot) has announced that it's partnering with Google-owned VirusTotal to scan skills that are being uploaded to Cla...
Learn how to work with AI, while strengthening your unique human skills that technology cannot replace The post What I Am Doing to Stay Relevant as a...
Germany's Federal Office for the Protection of the Constitution (aka Bundesamt für Verfassungsschutz or BfV) and Federal Office for Information Securi...
This is a video of advice for squid fishing in Puget Sound. As usual, you can also use this squid post to talk about the security stories in the news...
Amal Hussein returns to tell us all about her new role at Istari, what life is like outside the web browser, how she's helping ambitious orgs in aeros...
Once . Someone named “Vincenzo lozzo” wrote to Epstein in email, in 2016: “I wouldn’t pay too much attention to this, Schneier has a long tradition of...
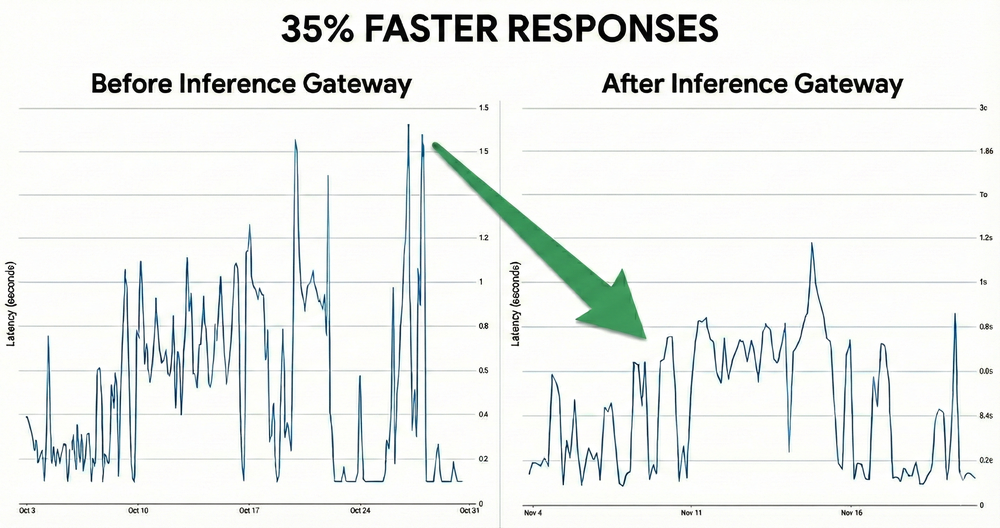
As generative AI moves from experimentation to production, platform engineers face a universal challenge for inference serving: you need low latency,...
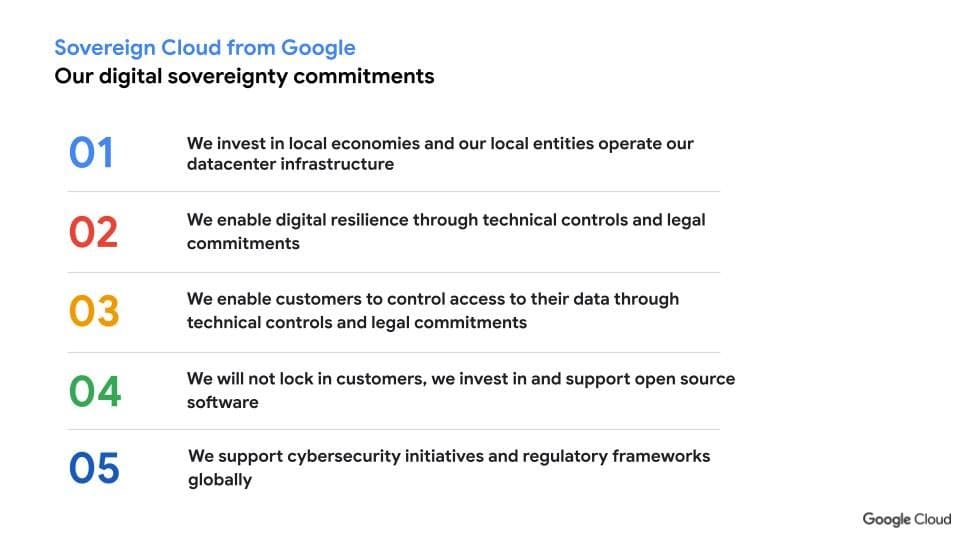
The global conversation about our digital future goes beyond technology; it’s about architecting a prosperous, secure, and resilient economy where the...

There’s no universally “best” design language. This section breaks down when Linear-style design works well, how to build beyond it (or start from Rad...
The real value lies in writing clearer code and using your tools right The post Pydantic Performance: 4 Tips on How to Validate Large Amounts of Data...
Cybersecurity researchers have taken the wraps off a gateway-monitoring and adversary-in-the-middle (AitM) framework dubbed DKnife that's operated by...
The Defense Industrial Base (DIB) and Federal System Integrator (FSI) communities operate under intense pressure. The mandate is clear: do more, faste...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has ordered Federal Civilian Executive Branch (FCEB) agencies to strengthen asset lif...
Showing 541 - 560 of 1268 articles