
Own a smart TV? These 13 features can dramatically improve your performance - here's how
Smart TVs are basically computers now, with their own hidden hacks, tips, and tricks. Here are a few I use to get the most out of my TV.

Smart TVs are basically computers now, with their own hidden hacks, tips, and tricks. Here are a few I use to get the most out of my TV.

A sysadmin’s guide to understanding sudo internals, common misconfigurations, and security hardening techniques that actually work Continue reading on...

Hi Vipul from The Hacker’s Log here 👋 Alright, let’s talk about money left on the table. 💸 Continue reading on OSINT Team »
SurrealDB's Poison Pill: Crashing the Database with a Single String Vulnerability ID: GHSA-XX7M-69FF-9CRP CVSS Score: 6.5 Published: 2026-02-12 A crit...

Clockwatching: Enumerating Directus Users via Timing Side-Channels Vulnerability ID: CVE-2026-26185 CVSS Score: 5.3 Published: 2026-02-12 A logic erro...
Introduction to IT Security Best Practices for Small Business As a small business owner, you understand the importance of protecting your company's se...
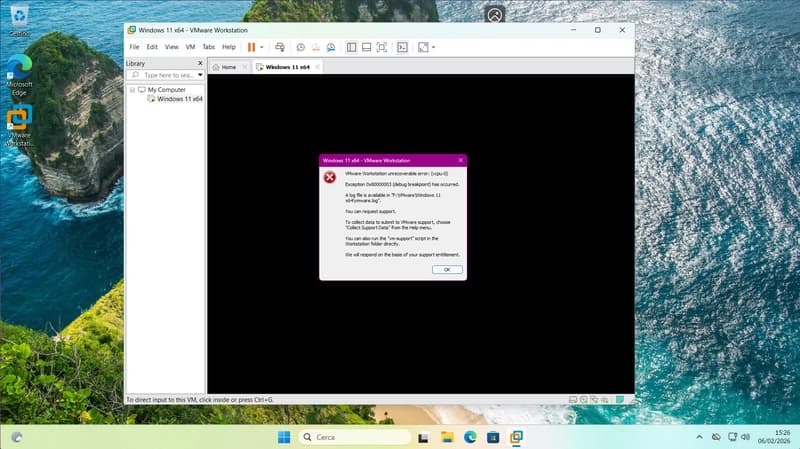
Introduction After upgrading to a modern system with full virtualization support — including VT-x, EPT, IOMMU, TPM 2.0, and Secure Boot — I expected e...
A practical guide to secrets management in the MCP ecosystem The Uncomfortable Truth About MCP Security The Model Context Protocol (MCP) is revolution...

Distillation technique lets copycats mimic Gemini at a fraction of the development cost.
Emails published by the Justice Department revealed cybersecurity veteran Vincenzo Iozzo emailed, and arranged to meet, Jeffrey Epstein multiple times...
Google on Thursday said it observed the North Korea-linked threat actor known as UNC2970 using its generative artificial intelligence (AI) model Gemin...
Cybersecurity researchers have discovered a fresh set of malicious packages across npm and the Python Package Index (PyPI) repository linked to a fake...
From prompt injection to deepfake fraud, security researchers say several flaws have no known fix. Here's what to know about them.

Add decentralized authentication to your web app in 30 minutes with Flowsta Auth. Zero-knowledge, privacy-first alternative to OAuth. Complete integra...
New York is contemplating a bill that adds surveillance to 3D printers: New York’s 20262027 executive budget bill (S.9005 / A.10005) includes languag...
Threat activity this week shows one consistent signal — attackers are leaning harder on what already works. Instead of flashy new exploits, many opera...
A new 2026 market intelligence study of 128 enterprise security decision-makers (available here) reveals a stark divide forming between organizations...
A significant chunk of the exploitation attempts targeting a newly disclosed security flaw in Ivanti Endpoint Manager Mobile (EPMM) can be traced back...

Every AI application processes external inputs and every external input is a potential attack vector. An attacker who can inject content into a knowle...
Apple on Wednesday released iOS, iPadOS, macOS Tahoe, tvOS, watchOS, and visionOS updates to address a zero-day flaw that it said has been exploited i...
Showing 1 - 20 of 107 articles