China-Linked Amaranth-Dragon Exploits WinRAR Flaw in Espionage Campaigns
Threat actors affiliated with China have been attributed to a fresh set of cyber espionage campaigns targeting government and law enforcement agencies...
Threat actors affiliated with China have been attributed to a fresh set of cyber espionage campaigns targeting government and law enforcement agencies...
The US National Reconnaissance Office has declassified information about a fleet of spy satellites operating between 1971 and 2006. I’m actually impre...
An innovative approach to discovering, analyzing, and governing identity usage beyond traditional IAM controls. The Challenge: Identity Lives Outside...
Many incident response failures do not come from a lack of tools, intelligence, or technical skills. They come from what happens immediately after det...
The Eclipse Foundation, which maintains the Open VSX Registry, has announced plans to enforce security checks before Microsoft Visual Studio Code (VS...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a critical security flaw impacting SolarWinds Web Help Desk (WHD) to...
Every time execution models change, security frameworks need to change with them. Agents force the next shift. The Unattended Laptop Problem No develo...
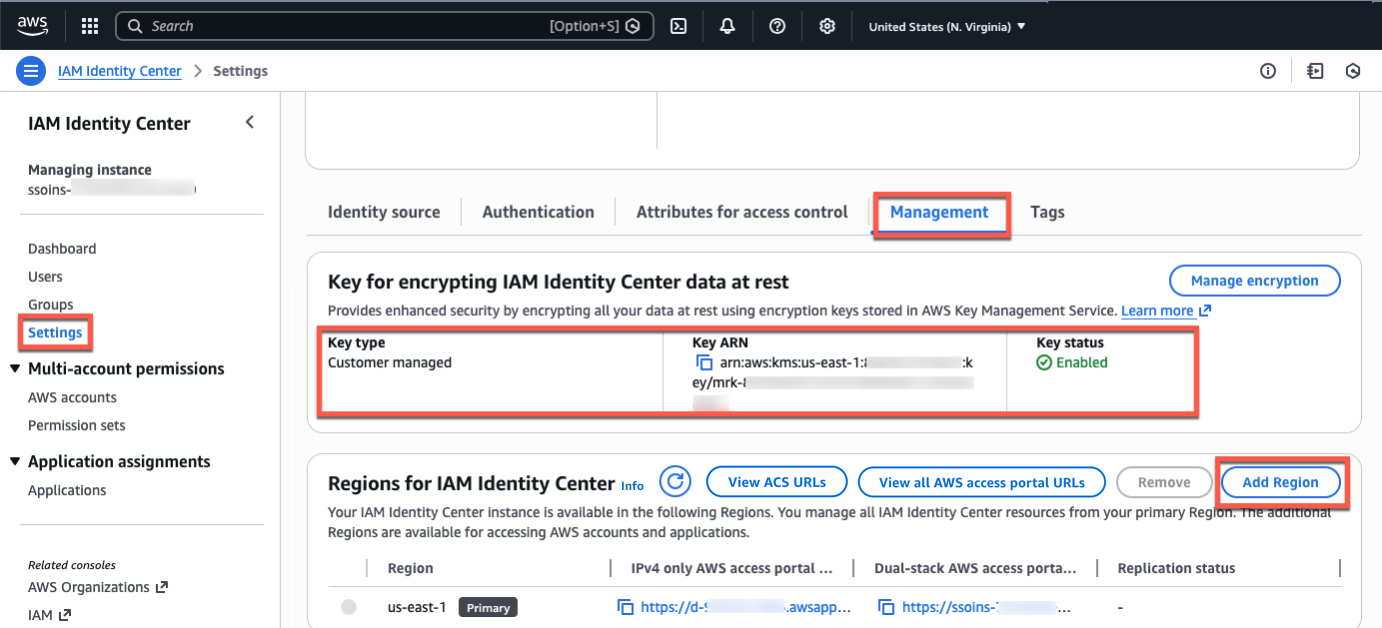
AWS IAM Identity Center now supports multi-Region replication of workforce identities and permission sets, enabling improved resiliency for AWS accoun...

What languages are growing fastest, and why? What about the projects that people are interested in the most? Where are new developers cutting their te...
Find out how HashiCorp Vault, HCP Vault Radar, and HCP Boundary can help you fulfill the PCI DSS 4.0 requirements checklist and get compliance certifi...
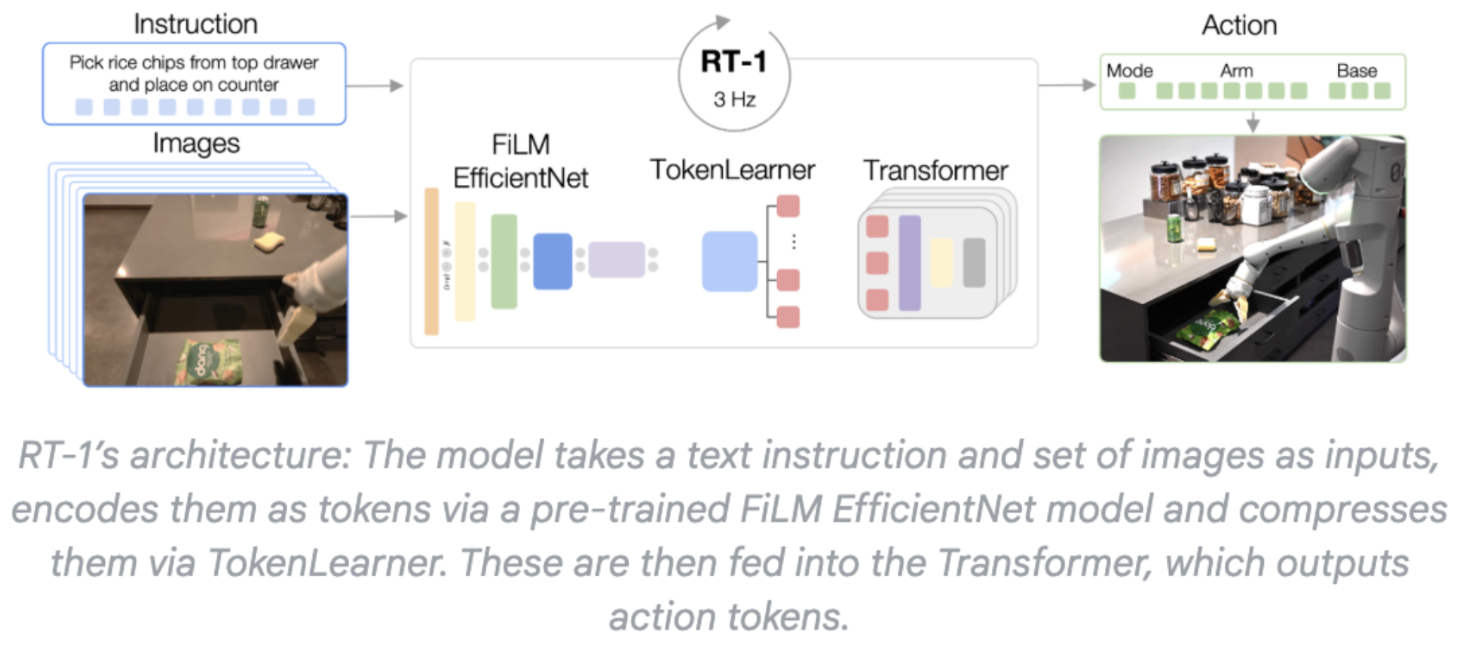
'Explore Vision-Language-Action (VLA) model advancements like Robotic Transformer-1 and \-2, OpenVLA, and π0 (Pi-zero).'
Cybersecurity researchers have disclosed details of a now-patched security flaw impacting Ask Gordon, an artificial intelligence (AI) assistant built...

You’d think that publishing a VS Code extension is an easy process, but it’s not. You have to publish your theme in at least two places. No Hassle Vis...
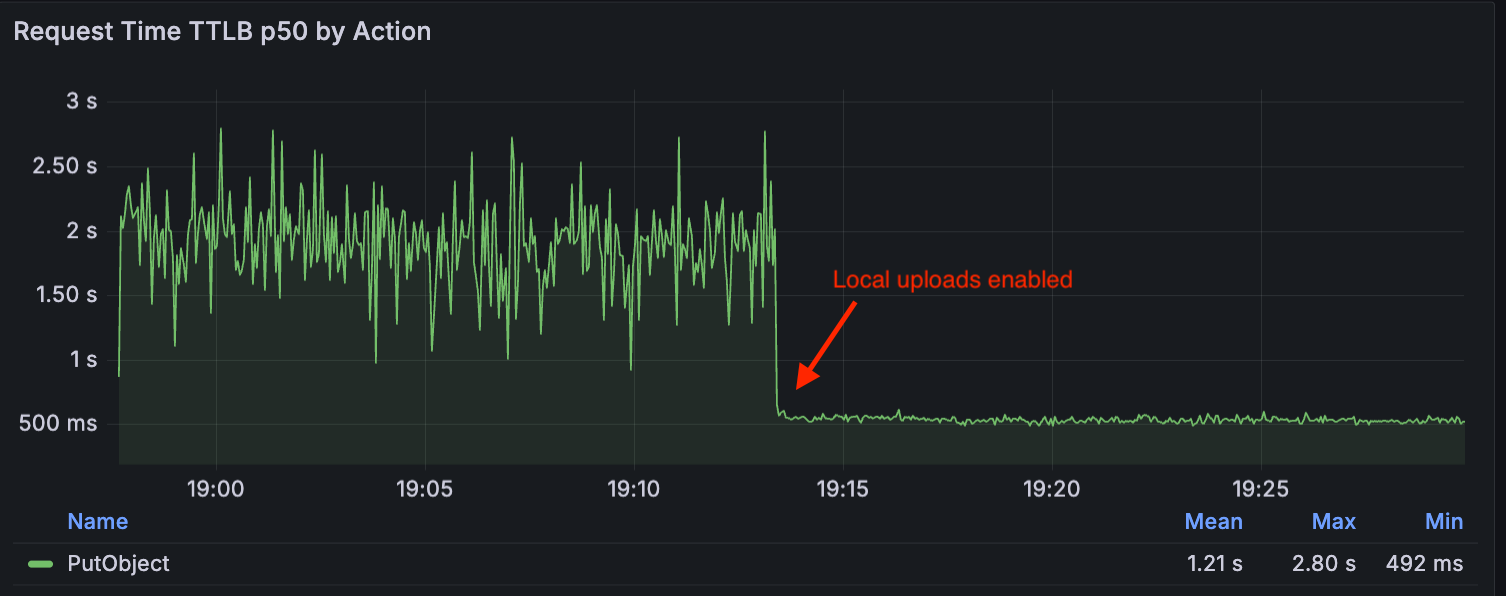
Local Uploads on R2 reduces request duration for uploads by up to 75%. It writes object data to a nearby location and asynchronously copies it to your...
In the standard Kubernetes model, a node’s suitability for workloads hinges on a single binary "Ready" condition. However, in modern Kubernetes enviro...

#771 — February 3, 2026 Read on the Web JavaScript Weekly Four Heavyweights Drop Updates Four stalwarts of the JavaScript ecosystem all shipped notab...
Jason Willems believes the tech monoculture is finally breaking, Don Ho shares some bad Notepad++ news, Tailscale's Avery Pennarun pens a great downti...

A prolific data ransom gang that calls itself Scattered Lapsus ShinyHunters (SLSH) has a distinctive playbook when it seeks to extort payment from vic...
We introduced Docker Sandboxes in experimental preview a few months ago. Today, we’re launching the next evolution with microVM isolation, available n...
We discuss the buzz around Clawdbot / MoltBot / OpenClaw, how app subscriptions are turning into weekend hacking projects, why SaaS stocks are crashin...
Showing 341 - 360 of 622 articles