How Samsung Knox Helps Stop Your Network Security Breach
As you know, enterprise network security has undergone significant evolution over the past decade. Firewalls have become more intelligent, threat dete...
As you know, enterprise network security has undergone significant evolution over the past decade. Firewalls have become more intelligent, threat dete...
Cybersecurity researchers have discovered a new supply chain attack in which legitimate packages on npm and the Python Package Index (PyPI) repository...
Artificial intelligence (AI) company Anthropic revealed that its latest large language model (LLM), Claude Opus 4.6, has found more than 500 previousl...
Open source components power most modern applications. A new generation of hardened container images can establish a more secure foundation, but even...

Deepika Manglani, VP of Product at the LA Times, talks about how she’s bringing the 140-year-old institution into the future. The post LaunchPod: Usin...

Stop losing action items in meetings. Granola AI notepad captures your notes, extracts tickets and decisions, and eliminates post-meeting friction for...

Minimal doesn’t always mean usable. This comparison shows how Linear-style UI keeps contrast, affordances, and structure intact, unlike brutalism’s ex...
The distributed denial-of-service (DDoS) botnet known as AISURU/Kimwolf has been attributed to a record-setting attack that peaked at 31.4 Terabits pe...
Sorting through the good, bad, and ambiguous aspects of vibe coding The post TDS Newsletter: Vibe Coding Is Great. Until It’s Not. appeared first on T...
Think of Continuous AI as background agents that operate in your repository for tasks that require reasoning. The post Continuous AI in practice: What...
Are the human-like cognitive abilities of LLMs real or fake? How does information travel through the neural network? Is there hidden knowledge inside...
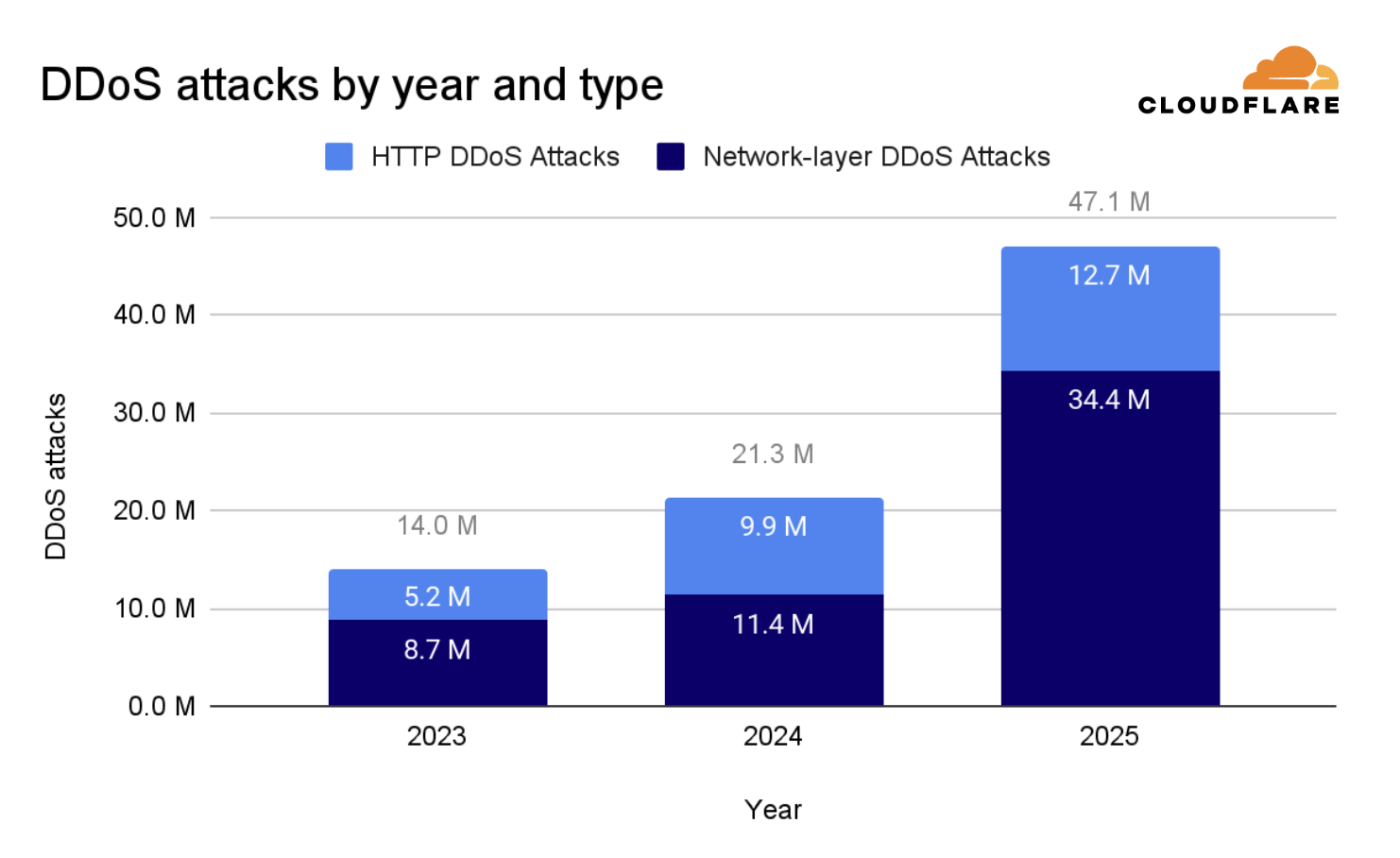
The number of DDoS attacks more than doubled in 2025. The network layer is under particular threat as hyper-volumetric attacks grew 700%.
This week didn’t produce one big headline. It produced many small signals — the kind that quietly shape what attacks will look like next. Researchers...
Hackers associated with the Chinese government used a Trojaned version of Notepad++ to deliver malware to selected users. Notepad++ said that official...
The elusive Iranian threat group known as Infy (aka Prince of Persia) has evolved its tactics as part of efforts to hide its tracks, even as it readie...
Prescriptive class name conventions are no longer enough to keep CSS maintainable in a world of increasingly complex interfaces. Can the new `@scope`...
A new, critical security vulnerability has been disclosed in the n8n workflow automation platform that, if successfully exploited, could result in the...
AWS launches Amazon EC2 C8id, M8id, and R8id instances backed by NVMe-based SSD block-level instance storage physically connected to the host server....
Microsoft on Wednesday said it built a lightweight scanner that it said can detect backdoors in open-weight large language models (LLMs) and improve t...
Threat hunters have disclosed details of a new, stealthy malware campaign dubbed DEAD#VAX that employs a mix of "disciplined tradecraft and clever abu...
Showing 321 - 340 of 622 articles