GHSA-XX7M-69FF-9CRP: SurrealDB's Poison Pill: Crashing the Database with a Single String
SurrealDB's Poison Pill: Crashing the Database with a Single String Vulnerability ID: GHSA-XX7M-69FF-9CRP CVSS Score: 6.5 Published: 2026-02-12 A crit...
SurrealDB's Poison Pill: Crashing the Database with a Single String Vulnerability ID: GHSA-XX7M-69FF-9CRP CVSS Score: 6.5 Published: 2026-02-12 A crit...
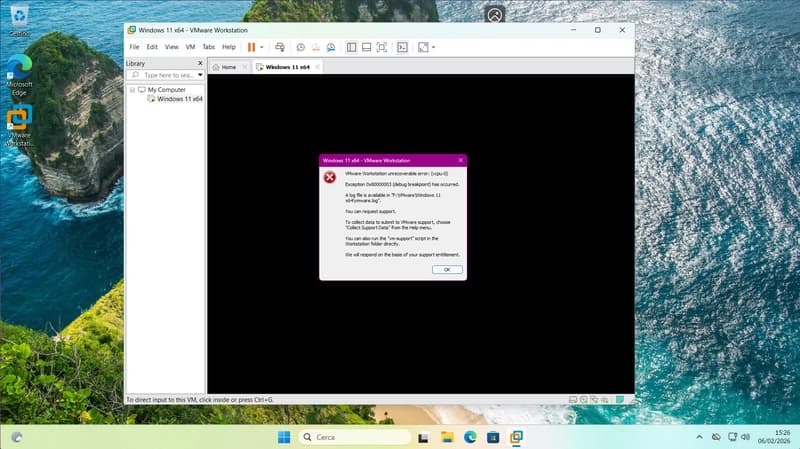
Introduction After upgrading to a modern system with full virtualization support — including VT-x, EPT, IOMMU, TPM 2.0, and Secure Boot — I expected e...

Distillation technique lets copycats mimic Gemini at a fraction of the development cost.
Emails published by the Justice Department revealed cybersecurity veteran Vincenzo Iozzo emailed, and arranged to meet, Jeffrey Epstein multiple times...
Google on Thursday said it observed the North Korea-linked threat actor known as UNC2970 using its generative artificial intelligence (AI) model Gemin...
Cybersecurity researchers have discovered a fresh set of malicious packages across npm and the Python Package Index (PyPI) repository linked to a fake...
From prompt injection to deepfake fraud, security researchers say several flaws have no known fix. Here's what to know about them.
Threat activity this week shows one consistent signal — attackers are leaning harder on what already works. Instead of flashy new exploits, many opera...
A significant chunk of the exploitation attempts targeting a newly disclosed security flaw in Ivanti Endpoint Manager Mobile (EPMM) can be traced back...

Every AI application processes external inputs and every external input is a potential attack vector. An attacker who can inject content into a knowle...
Apple on Wednesday released iOS, iPadOS, macOS Tahoe, tvOS, watchOS, and visionOS updates to address a zero-day flaw that it said has been exploited i...
Cybersecurity researchers have discovered what they said is the first known malicious Microsoft Outlook add-in detected in the wild. In this unusual s...

For the past week, the massive "Internet of Things" (IoT) botnet known as Kimwolf has been disrupting the The Invisible Internet Project (I2P), a dece...
Indian defense sector and government-aligned organizations have been targeted by multiple campaigns that are designed to compromise Windows and Linux...
I just noticed that the ebook version of Rewriring Democracy is on sale for $5 on Amazon , Apple Books , Barnes & Noble , Books A Million , Google Pla...
It's Patch Tuesday, which means a number of software vendors have released patches for various security vulnerabilities impacting their products and s...
Microsoft on Tuesday released security updates to address a set of 59 flaws across its software, including six vulnerabilities that it said have been...
Cybersecurity researchers have disclosed details of a new botnet operation called SSHStalker that relies on the Internet Relay Chat (IRC) communicatio...
The North Korea-linked threat actor known as UNC1069 has been observed targeting the cryptocurrency sector to steal sensitive data from Windows and ma...
Showing 1 - 20 of 66 articles