
A Governance Lens on Drift, Evidence, and Reliance.
Why Model Drift Is Often Behavioral Drift When people talk about model drift, they usually mean performance metrics changing over time. Accuracy drops...

Why Model Drift Is Often Behavioral Drift When people talk about model drift, they usually mean performance metrics changing over time. Accuracy drops...
You've built your MCP (Model Context Protocol) server. It connects to databases, APIs, maybe even cloud infrastructure. Your AI agent can now do real...
Article URL: https://www.techdirt.com/2026/02/12/ice-cbp-knew-facial-recognition-app-couldnt-do-what-dhs-says-it-could-deployed-it-anyway/ Comments UR...
Enterprise-class cloud systems seldom fail because of infrastructure constraints; rather, problems arise when architectural vision cannot scale to mat...
How review bottlenecks drain engineering productivity — data from LinearB, Google, DORA, SmartBear, and Meta. Your pull request has been open for two...
Open Source Radar (February 2026): Agentic AI, Zero Trust CI/CD, and Java GC Source: Analysis of Open Source For You (February 2026 Edition) The indus...
Eliminate secret zero and enable “secretless” workloads with Vault and workload identity federation. Replace static credentials with short-lived acces...

Buck Labs announced on February 12 that it would increase yields from 7% to 10% and transition from manual reward claims to automatic distribution. Th...
As AI workloads mature from experimental prototypes into business-critical systems, organizations are discovering a familiar problem: inconsistency at...

OpenAI described how it scaled PostgreSQL to support ChatGPT and its API platform, handling millions of queries per second for hundreds of millions of...
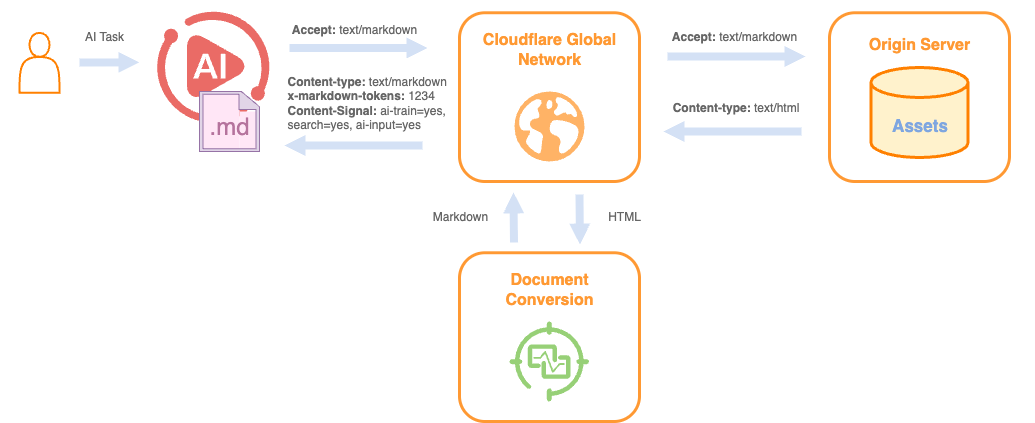
The way content is discovered online is shifting, from traditional search engines to AI agents that need structured data from a Web built for humans....
Introduction In the final quarter of 2025, Google Threat Intelligence Group (GTIG) observed threat actors increasingly integrating artificial intellig...
In an ideal DevOps world, every cloud resource is spawned from Terraform or Bicep. In the real world, we deal with “ClickOps.” An engineer manually tw...

WhatsApp has rewritten its media handling library in Rust, replacing 160,000 lines of C++ with 90,000 lines of memory-safe code for 3 billion devices....

Most eSIM plans don’t route traffic locally. Data often exits through centralized IP breakout hubs in another country, impacting latency, geo-IP accur...
This is the fifth interview of a SIG Architecture Spotlight series that covers the different subprojects, and we will be covering SIG Architecture: AP...

For more than a decade, Heroku defined what “developer-friendly deployment” meant. Push code, forget servers, and focus on shipping features. That pro...
Petitions demanding people get the chance to be released from ICE custody have overwhelmed courts throughout the US.
Information security outsourcing involves transferring part or all of an organization’s cybersecurity and IT infrastructure protection responsibilitie...
Deployment failures remain one of the most expensive and disruptive challenges in modern software development. Even with advancements in DevOps for tr...
Showing 1 - 20 of 112 articles